Model Open Systems Interconnection (OSI) was created by the International Organization for Standardization (ISO) That Provides a structured framework for logic-how processes Interact via a data communications network. Standards were the resource created for the computer industry to Communicate on different networks efficiently.
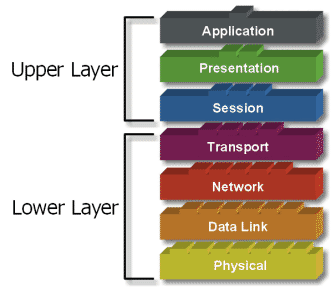
OSI Layer Model
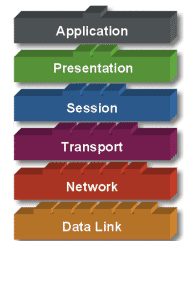
There are seven layers in the OSI model. Each layer is responsible for a particular aspect of data communications. For example, one layer may be responsible for establishing connections between devices, while another layer may be responsible for correcting the "errors" during the process of data transfer.
OSI Layer Model is divided into two groups: the upper layer and lower layer. "Upper Layer" focus on user applications and how files are represented on the computer. For Network Engineer, the main part of the attention is on the "lower layer. Lower layer is the essence of the actual data communication over a network.
“Open” dalam OSI
 “Open "in the OSI model is to express the interconnection of networks that perform regardless of hardware / hardware to use, all in accordance with standard communications software. This indirectly led to "modularity" (can be dismantled pairs).
“Open "in the OSI model is to express the interconnection of networks that perform regardless of hardware / hardware to use, all in accordance with standard communications software. This indirectly led to "modularity" (can be dismantled pairs).
Modularity
"Modularity" refers to the exchange of protocol at a certain level without affecting or damaging relationships or functions of other levels.
In a layer, protocols are interchangeable, and allows communication continues. These exchanges take place based on the hardware "hardware" from different vendors and a variety of different reasons or desires.
7 Layer OSI
Model OSI of 7 layer :
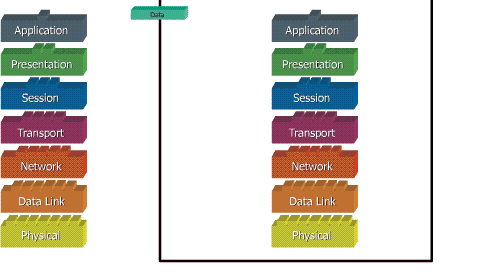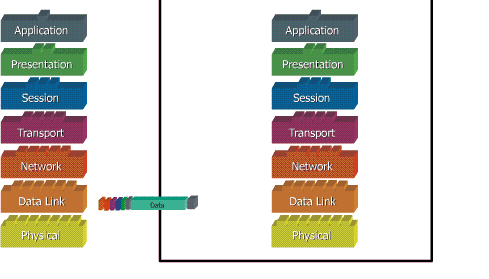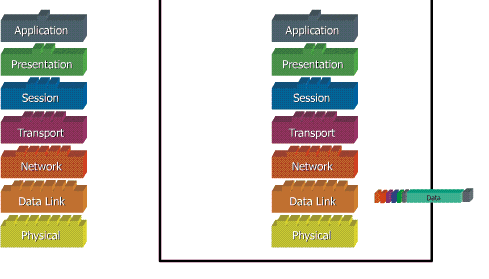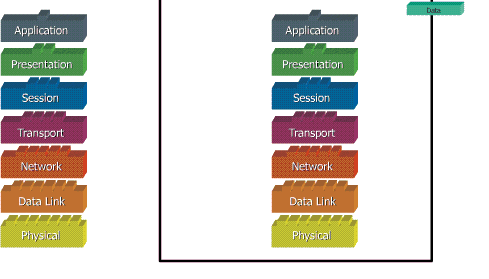
When data is transferred over the network, before the data must pass through all seven layers of a single terminal, from the application layer to physical layer, then at the receiver side, the data is through the physical layer to application. At the time of data through one layer of the sender, it will add a "header" while on the receiving end "header" was removed in accordance with layernya.
OSI Model
The main purpose of the use of the OSI model is to help network designers to understand the function of each layer are associated with the flow of data communications. Including the types of protoklol network and method of transmission.
The model is divided into 7 layers, with the characteristics and functions of each. Each layer must be able to communicate with the layer above it and below it directly through a series of protocols and standards.
OSI Layer Model
There are seven layers in the OSI model. Each layer is responsible for a particular aspect of data communications. For example, one layer may be responsible for establishing connections between devices, while another layer may be responsible for correcting the "errors" during the process of data transfer.
OSI Layer Model is divided into two groups: the upper layer and lower layer. "Upper Layer" focus on user applications and how files are represented on the computer. For Network Engineer, the main part of the attention is on the "lower layer. Lower layer is the essence of the actual data communication over a network.
“Open” dalam OSI
 “Open "in the OSI model is to express the interconnection of networks that perform regardless of hardware / hardware to use, all in accordance with standard communications software. This indirectly led to "modularity" (can be dismantled pairs).
“Open "in the OSI model is to express the interconnection of networks that perform regardless of hardware / hardware to use, all in accordance with standard communications software. This indirectly led to "modularity" (can be dismantled pairs).Modularity
"Modularity" refers to the exchange of protocol at a certain level without affecting or damaging relationships or functions of other levels.
In a layer, protocols are interchangeable, and allows communication continues. These exchanges take place based on the hardware "hardware" from different vendors and a variety of different reasons or desires.
Modularity |
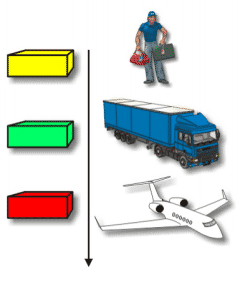 |
| As examples of the Inter Services / Courier. "Modularity" at the level of transport that is not important, how to package up to the plane. |
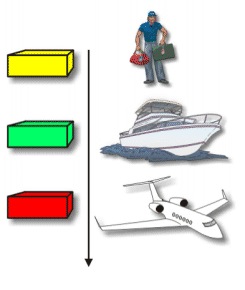 |
| Package to reach the plane, can be sent by truck or ship. Each of these ways, the sender still sends and hope the package arrived in Toronto. The plane flew to Toronto to bring the package regardless of how the package is delivered to the plane. |
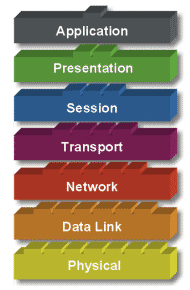
Model OSI of 7 layer :
- Application
- Presentation
- Session
- Transport
- Network
- Data Link
- Physical

When data is transferred over the network, before the data must pass through all seven layers of a single terminal, from the application layer to physical layer, then at the receiver side, the data is through the physical layer to application. At the time of data through one layer of the sender, it will add a "header" while on the receiving end "header" was removed in accordance with layernya.
OSI Model
The main purpose of the use of the OSI model is to help network designers to understand the function of each layer are associated with the flow of data communications. Including the types of protoklol network and method of transmission.
The model is divided into 7 layers, with the characteristics and functions of each. Each layer must be able to communicate with the layer above it and below it directly through a series of protocols and standards.
Model OSI | Keterangan |
 | Application Layer: Provides services for user applications. This layer is responsible for the exchange of information between computer programs, such as e-mail programs, and other service roads in the network, such as a printer server or other computer applications. |
 | Presentation Layer: Concerned with how data is converted and formatted for data transfer. Example conversion of ASCII text format for documents,. gif and JPG for pictures. This layer performs code conversion, data translation, encryption and conversion. |
 | Session Layer: Determines how two devices establish, maintain and manage the connection - how they relate to each other. Connections in this layer is called "session". |
 | Transport Layer: Responsible for breaking data into segments, logical connection "end-to-end" between the terminals, and provide error handling (error handling). |
 | Network Layer: Responsible for determining the network address, specify the route to be taken during the trip, and keep the network traffic congestion. The data in this layer-shaped package. |
 | Data Link Layer: Provides links to data, packaged into frames associated with the "hardware" and then transported through the media. It communicates with a network card, set the physical layer communications between connecting systems and error handling. |
 | Physical Layer: Responsible for the process data into bits and transfers them via the media, like cable, and maintain the physical connection between systems. A. OSI Reference Model LayerOSI reference model (Open Systems Interconnection) is a model of international protocol standards created by ISO (International Standards Organization). OSI model consists of seven layers of1. Phisycal layerIs unity layer or layers below the layer OSI reference model. In this layer the data received from data link layer frame and the form was changed to Bitstream to be sent a signal destination through communications media.At the receiver, this layer will change the signal from the sender to Bite and before being sent to the data link layer Bite converted into Bytes.2. Data Link LayerIs a second layer of the OSI reference model layer. In this layer the data received from the network layer in the form of a package that later diencapsulasi Frame, by providing layer-2 header. And then sent to phisycal layer to be forwarded to the recipient.At the receiver, this layer change the Byte into the Frame, the frame header will be removed (decapsulation), and then sent to the network layer into the Pack.3. Network layerIt is the third layer of the OSI reference model layer. This layer serves as delivering a package destination, known as the Routing.This layer controls the packet to be sent to the data link layer in a way to find the cheapest route and quick.4. Transport layerIt is the fourth layer of the OSI reference model layer. This layer is able to provide services such as Multiduplexing and Demultiduplexing, so that in this layer allows a host to serve more than one process.5. Session layerIt is the fifth layer of the OSI reference model layer. This layer is opened, care, control and conduct inter-node relationships. In this layer data transfer with a clear and linked with each other, but the quality of the data will experience delay, through-put. It is intended to maintain the quality of function-function is transport.6. Presentation layerIt is the sixth layer of the OSI reference model layer. Presentation layer associated with the syntax of data that is exchanged between applications, in order to overcome differences in data presentation format.7. Application layerIt is the seventh layer or layers of the OSI reference model layer. This layer is the application layer where user applications are placed, and this layer works with the Presentation Layer to be applied to data communication systems.B. ProtocolProtocol is the concept or rule that defines some functions that exist within a computer network that must be met by the sender and receiver for communication to take place properly.In the protocol there are things that need to be considered, namely;? Syntax is a data format, the scale of the propagating signal? Semantix is the control information and data errors that occur? Timing is the mastery of data transmission speed and sequenceC. Protocol on OSI Reference Model layerIn the OSI reference model layer, there are several layers of protocols in particular. These layers are1. Data link layerProtocol on the data link layer mengantur directly transfer between the nodes of data between two computers.The functions that support this protocol include:a. Transmission error detection and correctionb. Framing and link accessc. Reliable deliverryd. Flow controlFlow control is a technique used to control the process of sending frames from sender to receiver in order to avoid accumulation of the frame which causes the loss of the previous frame, this happens because the recipient has not taken the frame buffer to be received.Error control techniques at the data link in general there are two, namely:a. Error detection, there are three types, namely Parity, BCC and CRC are conducted on hardware, if there is error detection, the third flag will be on. If on the receiver will request re-transmission of data.b. Error correctionFrames that exist at the data link must include syncronisasi, a format in accordance with the control frame, in order to receive physical layer data link layer formats and a bit stream.The examples in the data link layer protocola. HDLC (High Level Data Link Control)b. Data Link layer on intenet consists of• SLIP (Serial Line IP)• PPP (Point to Point Protocol)c. Data Link layer in ATM2. Network layerInternet protocol has two architectures, namely:1. Internetworking connectionless protocolThe advantage of connectionless internetworking is:a. Flexible can be used with various types of connectionless network with little modificationb. Highly Roubus, if there are missing packets of data node can be obtained via other nodesc. It is appropriate if the requested connection is a connectionless transport layer2. Connection Internetworking ProtocolExamples of Connection Internetworking Protocol are:a. ICMP (Internet Control Message Protocol) asked to send error messages and other conditions that takes into account the special attentionb. ARP (Address Resolution Protocol) in charge of finding the hardware address of a host with a specific IP addressc. RARP (Reverse Address Resolution Protocol) in charge of translating hardware addresses as the IP address of a host.d. IP (Internet Protocol) duty to provide the best way to bring a datagram from the source destination, regardless of whether the machines in question are on the same network or not, or whether there are other networks between sources with the goal or not.3. Transport layerTransport services are implemented by the transport protocol used between two entities, this protocol resembles the protocol at the data link in terms of error control, sequencing, and control the flow of data.In addition to these equations and the transport protocol data link protocol also have differences.Differences transport protocol with protocol data link available from:a. The environment in which it operates protocols. At the data link two routers communicate directly through physical channels and do not need to be addressing to determine the router to communicate, while at the transport layer is replaced by the physical channel and the required subnet addressing to determine the router to communicate.b. Allocating buffers. At the data link buffer remains allocated in each channel so that the new frame will always get a buffer that can be used. At the transport layer jaka do not attract the same with the data link, because the transport layer connection occurs with a large amount.At the transport layer, the Internet has two main protocols, namely:a. TCP (Transmition Control Protocol) is a protocol that is connection oriented. Each byte in the TCP connection has a 32 bits serial number itself.Entity TCP sender and receiver exchange data in the form of segments, each segment header has a fixed size of 20 bytes followed by zero or more bytes of data. TCP software decides the size, segment, and can accumulate data from several writing into a segment, or dismember from a writing data into several segments.There are two things that limit ukurun segmenta. Each segment, including the TCP header, must fit the IP playload 65,535 bytesb. Each network has a MTU (Maximum Transfer Unit) which is generally a few thousand bytes that specify the maximum size segment.If a larger segment of tissue in its path, then the segment can be split into segments by a router miraculous.TCP connections in use headshake three directions. To establish a connection, the server, passively waiting for incoming connections by executing a primitive-primitive listen and accept, either by specifying a specific source or do not specify anything at all. On the client executes the connect primitive, which specifies the IP address and port where the connection will be made, the maximum TCP segment size to be received, and optionally some user data such as passwords. Primitive connects sends TCP segment with SYN bit is switched on and the ACK bit in a state of passive and waiting for a response.Management window in TCP is not directly related to the acknowledgments as in most of the data link protocols. For example, the receiver who has a buffer 4096 bytes, when a sender transmits segments of 2048 bytes are received correctly, then the recipient will mengacknowladge this segment. However, since now only has a 2048 recipient of buffer space, then the recipient will offer a window of 2048 bytes that begins on the next byte expected.c. UDP is a connectionless protocol that nature.4. Session layerThe most important function is to bring the session layer semantics of user interaction service session melelui relationships with other users. The interaction between the session entities by way of mutual exchange Session Protocol Data Unit (SPDU) through the relationship of logic, that they are related mainly ubntuk support the relationship between the two service user's session.These exchanges can occur if both follow the procedure syntax and semantics of the session protocol. Protocol also specializes to the events that led to SPDU sent, or activities conducted by the entity when receiving SPDU ssession.SPDU parameters consist of:a. Parameter Group units owned by the encode parameters groupParameter unit group consists of three fields, namely:• Field that identifies the group indicator parameter group that has been encoded.• Field length indicator which identifies the length of the parameter group that has been encoded.• One or more parameters of the unit if any.b. Parameter owned unit encodes a single parameterParameter unit consists of three fields as follows:• Field parameters of indicators that identify the parameters that have been encoded.• Field parameters that identify the length indicator of the value of the parameter.• The contents of the parameter itself if any.Fields are usually used in the field of communication relationships, which become SPDU parameters consist of:a. SPDU SPDU type indicator field implementb. Length indicator field implement parameter lengthc. SPDU field parameters apply one or more encode parametersd. User information field is applied and if there is SPDU5. Presentation layerVirtual Terminal Protocol (VTP) is an example of the presentation layer protocol.The function of VTP is a package of programs in which specific terminal converted into a common function that can be used by any vendor. This software package is part X28/X29/X.3 called PAD (Packet Assambly Deassambly)X.3: control operationX.28: terminal emulatorX.29: Host emulatorThe function of VTP for presentation layer are:a. Create and maintain data structuresb. Translating the terminal characteristics to the standard form6. Application layerIn this layer there are two types of protocols are often used, namely:1. SNMP (Simple Network Management Protocol)This protocol serves to simplify a complex network system to be simple. All information about the network will exist in each group being placed at the Management Information Base (MIB)In general, this protocol shall:• Restruktur network toward the easily controlled by dividing the upper parts• All information stored in MIB• Strong security• Have privacy in each group or between groups• Clock Synchronization• Having access controlSNMP is a component that plays an important role in the Network Management System which is a collection of tools to memonitori and control network which has the properties:• An operator interface capable of providing the commands to complete part or all network management work.• Part of the hardware and software needed for management can be merged into existing equipment.Components of Network Management System are:• Management of terminal or manager is a stand-alone However the equipment has the ability to apply to the distribution system, terminal management work as liaison between a network manager with network management systems.• Agent, which is the key platforms such as hosts, bridges, routers, and hubs that may be supplied with software agents, so it can be managed from a working terminal management.• Management Information Base• Network Management ProtocolWork terminal management and agent are connected by a Network Management Protocol. SNMP is used for network management of TCP / IP, while for OSI-based network is used CMIP (Common Management Information Protocol), ie SNMPv2 SNMP version that has been perfected, could have been used at the network based on TCP / IP and OSI.2. FTP (File Transfer Protocol)This protocol aims to transfer a file or part of the file using the FTP command is done by adding the drivers on the operating system so that the operating system can be used interactively by the user while online. This protocol often includes a layer 5.6, and 7 together to function as a user application to directly access transport layer for the file sent.ISO uses the FTAM standard FTP (File Transfer, Access and management) in the sending, accessing and managing files. This standard has three characteristics, namely:a. Virtual Filestore Definition, namely the structure of the file, an attribute that indicates a file, the actions of the handling of files and file elements.b. File Service Definition, which defines the services available to the user to access and manipulate the virtual file.c. File Protocol Specification, which serves to provide a direct support FTAM service. There is a one-one mapping from simple service to the protocol data unit. This section will do the setup on the connection and insert a checkpoint on the flow of data.There are three possible file transfer process, namelya. Users will transfer files from himself to others that exist in networkb. Users will transfer files from other users to himselfc. Users will first transfer the file from itself to other users, or from the second user to a third user of the first user command.Files are transferred by the user can be:a. The data inside the fileb. Data and file structurec. Data and file structures and other attributes, such as access control lists, index, update, and othersService that can be generated by the FTP is:a. Access controlb. Processing modec. File Name Fasilitiesd. Alternating Operatione. File Management Fasilitiesf. Error Recoveryg. Flow Controlh. File Structuri. Status Report |